Access Management
Access management, pivotal in safeguarding your organization's assets, entails the meticulous control and monitoring of resource access. Through authentication, authorization, and robust policies, we ensure only authorized users access critical systems and data. Our comprehensive approach fosters security, efficiency, and regulatory compliance within your operations.
We offer expert guidance and strategic consulting services to help organizations develop robust IAM strategies aligned with their business objectives. Our consultants work closely with clients to assess their current IAM infrastructure, identify gaps, and devise tailored solutions to enhance security and efficiency.
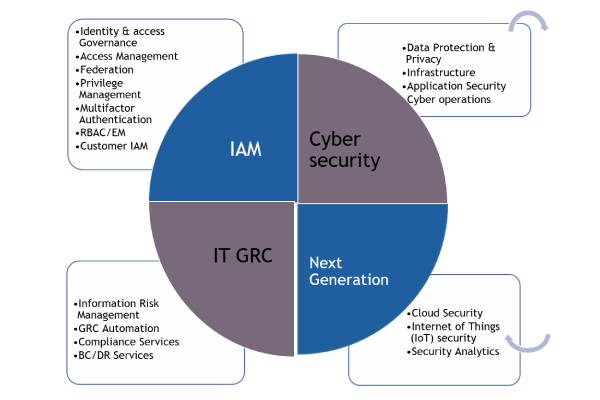

Identity Access Management
Identity Access Management (IAM) is the cornerstone of modern cybersecurity strategies, providing granular control over user access to digital resources. Our IAM solutions offer seamless authentication, authorization, and accountability mechanisms, safeguarding your organization's data and systems. With customizable policies and advanced analytics, we empower businesses to manage identities effectively, ensuring security, compliance, and operational efficiency
We offer expert guidance and strategic consulting services to help organizations develop robust IAM strategies aligned with their business objectives.
Identity Governance & Administration
Identity Governance & Administration (IGA) is pivotal for streamlined access management. Our solutions offer comprehensive oversight of user identities, permissions, and compliance. With centralized identity governance processes, we empower organizations to mitigate risks and optimize efficiency.
We provide comprehensive Identity Governance and Administration solutions designed to manage user identities, roles, and access privileges effectively. Our IGA services enable organizations to enforce access policies, streamline compliance processes, and mitigate security risks.


Privileged Access Management
Privileged Access Management (PAM) is vital for secure access control. Our solutions offer robust oversight of privileged accounts, enhancing security and compliance. With centralized PAM processes, we empower organizations to mitigate risks effectively.
We provide advanced Privileged Access Management solutions to safeguard critical systems and sensitive data from unauthorized access. Our PAM services help organizations enforce least privilege principles, monitor privileged activities, and mitigate insider threats effectively
Multifactor Authentication
Multifactor Authentication (MFA) enhances security by requiring multiple forms of verification. Our MFA solutions bolster access control, ensuring only authorized users gain entry. With added layers of protection, we fortify defenses against unauthorized access and data breaches.
We specialize in authentication including Single Sign-On, multi-factor and password-less solutions to simplify user authentication
Connect With Us
-
Contact
+1 (720) 339-2386
-
Mail
support@mrtechnosoft.com
-
Location
9800 Mount Pyramid Court, Suite 400, Englewood, Colorado 80112, USA









